Ciscoda tarmoq qurilmalar xavfsizligi
Cisco qurilmalarini ruxsatsiz kirishdan himoya qilish uchun bir nechta parol turlari qo’llaniladi. Bular konsol uchun parollar, telnet va ssh orqali ulanish uchun parollar, shuningdek, qurilmaning pravilage rejimiga kirish uchun parolni belgilashni turlari mavjud. Ushbu parol turlari barcha tarmoq qurilmalariga o’rnatiladi.
Konsol rejimga parol o’rnatish
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#line console 0
Router(config-line)#password MyPassword
Router(config-line)#login
Router(config-line)#exit
Router(config)#exit
Router#
Telnet yoki SSH ga parol o’rnatish
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#line vty 0 4
Router(config-line)#password MyPassword
Router(config-line)#login
Router(config-line)#exit
Router(config)#exit
Router#
Pravilege rejimga parol o’rnatish
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#enable password MyEnablePassword
Router(config)#exit
Router#
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#enable secret SecretPassword
Router(config)#exit
Router#
Parollarni shifrlash xizmati
Router(config)#service password-encryption
Router(config)#exit
Router#show running-config
Building configuration…
…
enable secret 5 $1$mERr$KnP4XAeHLfyk/RPXMCetr0
enable password 7 080C556B0718071B173B0D17393C2B3A37
…
line vty 0 4
password 7 080C557E080A16001D1908
login
…
SSH vs TELNET
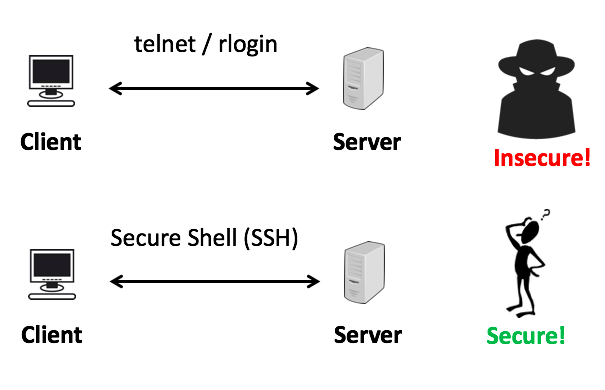
TELNET
ROUTER sozlamasi quyidagicha:
Router>enable Router#conf t Router(config)#int GigabitEthernet 0/0 Router(config-if)#no shutdown Router(config-if)#ip address 192.168.10.1 255.255.255.0 Router(config-if)#exit Router(config)#line vty 0 15 Router(config-line)#password 123
SSH
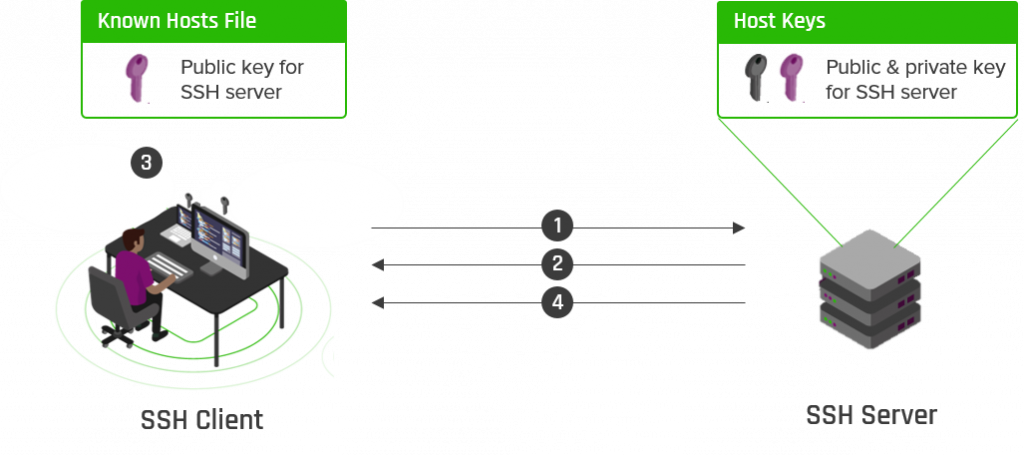
ROUTER sozlamasi quyidagicha:
Router(config)#int GigabitEthernet 0/0 Router(config-if)#no shutdown Router(config-if)#ip address 192.168.10.1 255.255.255.0 Router(config-if)#exit Router(config)#hostname R R(config)#ip domain-name R.uz R(config)#crypto key generate rsa 1024 R(config)#enable secret cisco R(config)#username cisco secret 123 R(config)#ip ssh version 2 R(config)#ip ssh time-out 30 R(config)#ip ssh authentication-retries 2 R(config)#line vty 0 15 R(config-line)#transport input ssh R(config-line)#login local
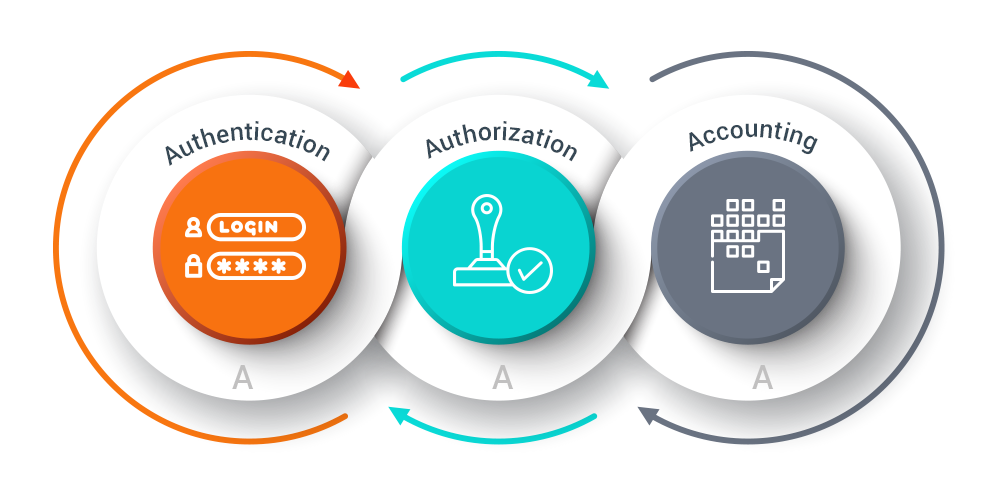
AAA serveri
Qurilmaga murojat qilishning ikki xil usuli bor ular local va AAA server orqali amalga oshiriladi. AAA (Autentification, authorization, accounting) autentifikatsiyadan o’tib avtorizatsiyadan o’tgach xizmatlardan foydalanish huquqiga ega bo’lish deganidir. AAA ning asosiy ikkita protokoli keng tarqalgan va ommaviy tarzda ishlatiladi. Ular RADIUS va Tacacs (Tacacs+) protokollaridir.
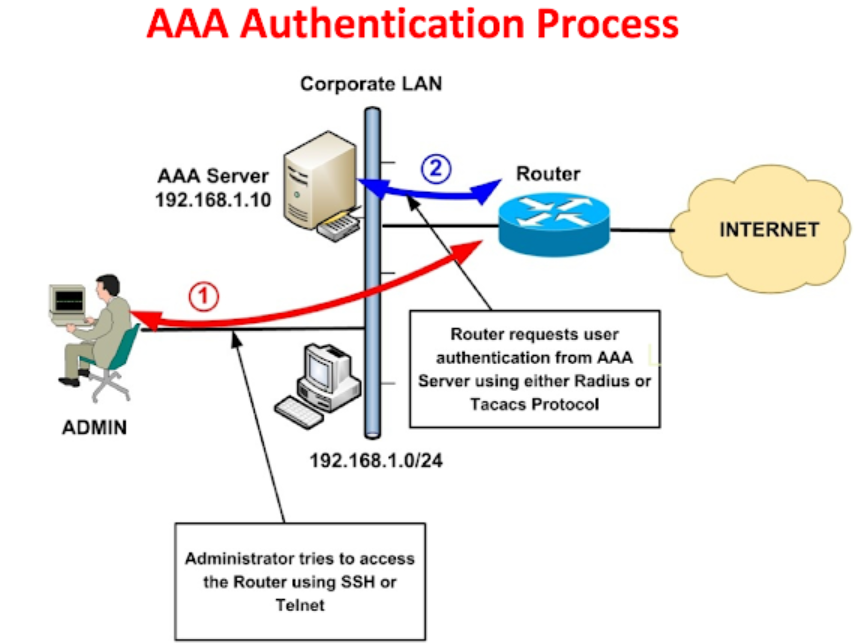
Radius vs Tacacs

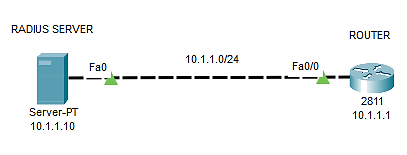
Radius serverni sozlash:
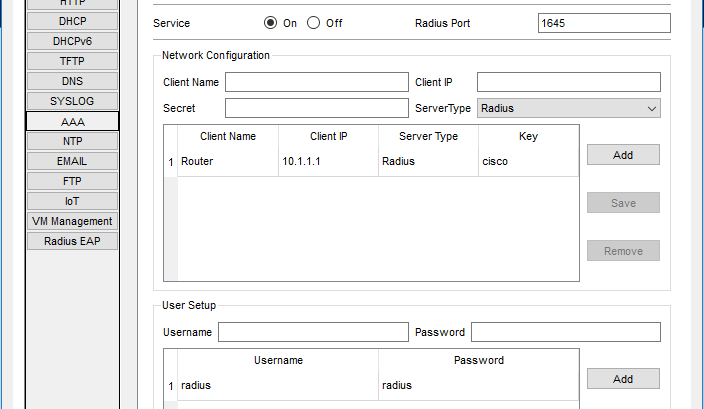
Routerni sozlash:
Router(config)#int fa0/0
Router(config-if)#no shut
Router(config-if)#ip address 10.1.1.1 255.255.255.0
Router(config)#aaa new-model
Router(config)#radius-server host 10.1.1.10 key cisco
Router(config)#aaa authentication login default group radius local
Router(config)#username local password local

